Defending in depth with a consolidated security platform
This is the second part of our series with CyberQP. Read Part 1 here.
Introduction
Considering the number of headlines involving successful cyberattacks on organizations big and small, one might think that attacks could happen overnight. The reality is that cyberattacks result from weeks to months’ worth of work and generally follow a prescriptive process known as the cyberattack lifecycle or kill chain.
In this blog, we will detail each step in the kill chain and how organizations can leverage a cloud security platform paired with privileged access management (PAM) to defend themselves at each stage.
Key Takeaways
- Organizations can employ a defense-in-depth (DiD) approach to cover the attack vectors preyed upon throughout the kill chain.
- Combining DiD with zero trust security ensures multiple layers of protection across the entire stack.
- A comprehensive security platform like Todyl and a privileged access management solution like CyberQP enable organizations to consolidate defense-in-depth and zero trust into a streamlined stack.
Analysis
There are eight stages involved in a typical cyberattack. Here’s what each entail, as well as how Todyl and CyberQP work in concert to defend against them.
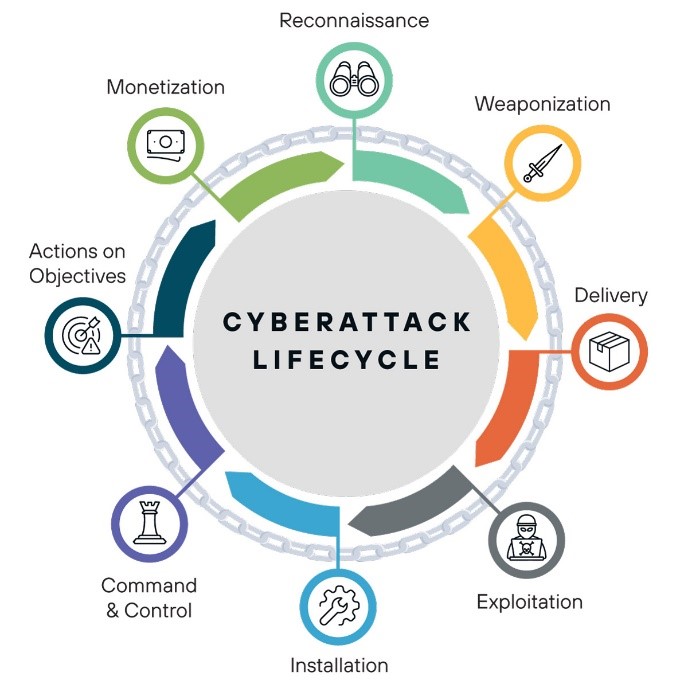
The Kill Chain
- Reconnaissance
Before an attacker begins, they need to understand their target. This stage involves research and investigation of an organization, identifying its valuables, environments, and potential vulnerabilities.
- Weaponization
Next, the hacker develops how they will attack the organization. Commonly, this might involve pairing malware like a remote access trojan (RAT) or other infection with a downloadable PDF or a macro-enabled Microsoft Office document.
- Delivery
Now, the attacker determines the best way to sneak their weapon into the environment. Business email compromise (BEC), phishing, social engineering, and other methods are all prominent modes today’s attackers use.
- Exploitation
This is the turning point of the cyberattack lifecycle when preparation turns to action. A successful delivery enables the bad actor to build off the intelligence gathered to this point to exploit vulnerabilities and make their way to sensitive systems.
- Installation
Attackers leverage their headway within an environment to deploy the weapon. From here, attackers will also seek out any backdoors they can use to establish persistence.
- Command & control
At this point, the attacker is successfully within the environment, having delivered their payload and engaging the weapon. They usually take advantage of their position within the network to remotely clean up their tracks while having access to other systems within the network.
- Actions on objective
Lastly, the bad actor completes their objective, exfiltrating or deleting data, as well as potentially affecting other systems down the chain.
- Monetization
Now that the attacker has completed their objective, they seek out ways to capitalize and profit off their findings, whether that be holding data ransom or selling it to the highest bidder.
What you can do today: Defense-in-Depth
Using a consolidated security platform in concert with a privileged access management solution helps organizations tackle the entirety of the kill chain with a layered, defense-in-depth approach.
Defense-in-depth is a security framework that relies on multiple stages of security technology, along with sophisticated processes and people training, to put up barriers against attackers. Because of these layers, attackers have difficulty moving along the kill chain and stealing sensitive data and other information.
CyberQP lets you establish PAM across your organization’s identities, with fine-tuned control over what end users can access based on roles. This allows you to minimize your attack surface and reduce lateral movement.
Then, using Todyl, you can implement tight security controls at the endpoint, network, and application layers. With top-down observability across the entire environment, using both Todyl and CyberQP lets you establish a true defense-in-depth approach to securing your organization.
Conclusion
By establishing a defense-in-depth security framework, you can create layers of protection that help you detect and respond to threats from all stages of the kill chain. Leveraging CyberQP and Todyl allows you to build a defense-in-depth approach while consolidating your security stack, saving you time and money without compromising on effective security and identity controls.
Learn more about how consolidating through Todyl and CyberQP can benefit your organization. Watch this webinar to hear how MSPs are using consolidation to support their clients and improve their business.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



