Capabilities of Different SASE Approaches
As organizations look to address their cybersecurity maturity and adhere to a security framework, many today choose zero trust security, including the US Government. With a “never trust, always verify” mindset and a supporting solution stack, IT admins and security teams leverage Zero Trust to prevent unauthorized access to resources as well as lateral movement within the network. In that way, Zero Trust reduces the attack surface area that a bad actor can access at any given point in time.
When it comes to achieving Zero Trust Network Access (ZTNA), Secure Access Service Edge (SASE) solutions provide an excellent way to set controls and policies that support the “never trust, always verify” mindset. There are a variety of different approaches taken by SASE vendors when it comes to product capabilities, however, they all point toward the common goal of securing access. This blog will break down the capabilities of each of these SASE implementations to help you determine which one will best suit your needs and further your zero trust journey.
Capabilities of SASE implementations
So, what is SASE exactly? Coined in 2019, Gartner defined the SASE framework as a “cloud-based cybersecurity solution that offers comprehensive WAN capabilities with comprehensive network security functions, such as Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), Firewall as a Service (FWaaS), and ZTNA, to support the dynamic secure access needs of digital enterprises.”
Later, in 2021, Forrester laid out a similar framework called Zero Trust Edge, which “securely connects and transports traffic, using Zero Trust access principles, in and out of remote sites leveraging mostly cloud-based security and networking services.”
SASE ultimately extends beyond these definitions in the real world, centered around the common goal of securing access to network resources through whatever means. As such, SASE providers offer a wide variety of approaches that address some or all the facets laid out by Gartner/Forrester. The three most common approaches providers take include:
- A Zero Trust Overlay Network, or ZTON
- A Software-Defined Perimeter, or SDP
- An Identity-Aware Proxy, or IAP
Let’s explore each of these in greater detail.
Zero Trust Overlay Network
A ZTON consists of a software-driven mesh network that exists in a layer above the traditional network. It acts as a buffer between users and network resources. Because it exists in the cloud, a ZTON is an effective way to control access to remote infrastructure environments.
When users attempt to access a specific resource, they must first access the ZTON, creating a point where they must prove trust by authentication, adhering to Zero Trust. Once a user identity is authenticated, the ZTON then creates a secure access tunnel between the user and the specific network resource. On the backend, IT/SecOps teams can control who can access what resources or other aspects of the network through the ZTON by enforcing policies based on identity.
Although effective for Zero Trust Network Access, ZTONs lack several key security features called out in analyst definitions of SASE, namely SWG, CASB, and FWaaS, along with other functionality.
Software-Defined Perimeter
An SDP imitates the network of old, creating a boundary around network resources much like the four walls of an Ethernet-connected office. Like with said office, users “badge in” to the SDP with their trusted identity. Once a user’s identity is authenticated, they can access their requisite resources without friction.
To achieve this, an SDP obfuscates network infrastructure through software instead of hardware for extensibility. It works via a downloaded agent or by connecting to a VM or appliance that runs the SDP.
Again, like with a ZTON, SDPs are effective Zero Trust Network Access controllers, but can also miss out on other key security features.
Identity-Aware Proxy
IAPs are the broadest and often most feature-rich SASE solutions. They rely on PoPs (points of presence), localized servers that users of a given city or region (e.g., Chicago, US West, EMEA, Oceania) connect to in order to access a cloud network. Like with all the other implementations, IAPs need end users to authenticate via their trusted identity. Similar to an SDP, once a user has access to the IAP via the cloud network, they can access their intended resources.
In the case of an IAP, each PoP is a node in a larger network that may have security controls like an SWG, CASB, or others built into it. In that way, IAPs consolidate network security functions while also enabling secure access to remote resources by remote users. This provides extensibility and peace of mind that users’ network security can travel with them, regardless of where they go.
Comparing ZTONs, SDPs, and IAPs
We developed the below comparison graphics to help further explain the intricacies of different SASE approaches:
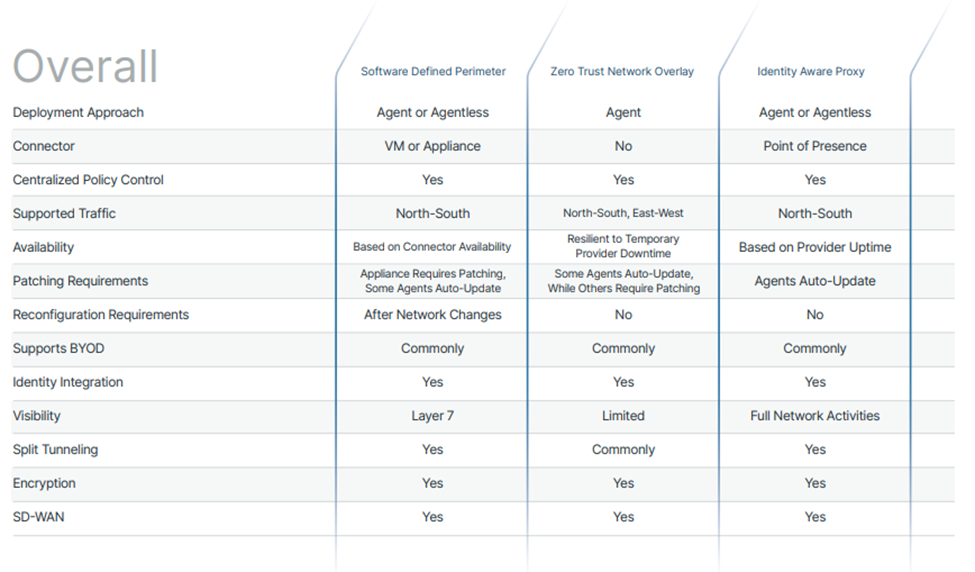

In each scenario, the common underlying theme behind these implementations is identity-based authentication, used to ensure users are who they say they are. Although important, with a Zero Trust approach, this is not enough to fully ensure security. In order to further enforce Zero Trust, least privilege access policies should also be enforced.
Deciding on the best SASE implementation for you
In practice, each of these implementations is fairly similar, but given the specific complexities of your IT environment, you may opt to leverage one or another to best suit your needs. You may even find you need a solution that combines multiple aspects of each implementation into one platform.
The team at Todyl has years of expertise in rolling out SASE and ZTNA across businesses of all shapes and sizes, and we’re happy to assist you in your journey, too. To gain a deeper understanding of what capabilities to look for in a SASE implementation, download our SASE eBook.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



