Todyl Success Story: Genuine Tech Group Penetration Test
Genuine Technology Group is a leading MSP and trusted advisor to clients across industries, including local governments and critical infrastructure where security is mission critical.
Ernest Murry, Genuine’s Chief Technology Officer with over 20 years of experience managing MSPs, recently led the company’s efforts to implement an enhanced security stack. Genuine already relied on Todyl’s Secure Access Service Edge (SASE) to connect and protect its clients working remotely and in-office. Recognizing the need to further optimize security postures, Ernest evaluated different solutions and vendors before making the strategic decision to implement three modules from the recently launched Todyl Security Platform, including:
- Endpoint Security that combines Endpoint Detection & Response (EDR) and Next-Generation Anti-Virus (NGAV) with Ransomware, Malware, Malicious Behavior, and Memory Threat Protection.
- Security Information and Event Management (SIEM) that ingests and analyzes logs from any data source, helping partners identify breaches, hunt for threats and vulnerabilities, and investigate alerts through a single-pane-of-glass.
- Managed eXtended Detection & Response (MXDR) that provides a unique, personalized service focused on prevention, detection, and response.
Following the implementation, one of its clients requested a penetration test to assess the effectiveness of Genuine’s security stack and system configuration. The goals of the test included:
- Documenting and demonstrating attack vectors
- Quantifying the impact of successful attacks through active exploitation
- Identifying specific vulnerabilities to remedy and improve security
- Recommending ways to improve Genuine’s overall security posture
Penetration test play-by-play
Ernest and the penetration tester designed the test as an assumed breach. They decided the tester would attempt to spread laterally across Todyl’s Secure Global NetworkTM (SGN) Cloud Platform, the backbone of Todyl’s SASE module, to a hosted server in the client’s data center.
The SGN features Zero Trust Network Access (ZTNA). This capability enables organizations to securely access resources from everywhere over fast, secure, and reliable connections. In this case, Genuine configured SASE with ZTNA, so the client can only access the data center over the SGN, helping to greatly reduce the attack surface area by eliminating public-facing access to the datacenter.
For this testing scenario, it is assumed that the threat actor gained access to the client’s network. The goal is to determine what data they can exfiltrate, where they can move laterally, and what payloads and executables they could run on the device. Assumed breaches give Genuine a comprehensive assessment of any internal network vulnerabilities from the perspective of a threat actor.
To start the assumed breach, Ernest shipped a laptop and user log-in directly to the tester, who started executing multiple payloads and executables to bypass Todyl’s Endpoint Security and gain persistent access. The Malware Prevention in Todyl’s NGAV module blocked the first payload, and within 10 minutes, the Managed Extended Detection & Response (MXDR) team alerted Ernest in Slack, unaware that a penetration test was taking place.
The MXDR team gave Ernest a play-by-play of the tester’s attempts, including the host’s name, path, and parent process. During their investigation, the team uncovered an unknown hash for the binary “Windows_Update.exe.” This file was not signed by Microsoft and was not recognizable by any reputation-based hash lookup services.
Unrecognizable hashes can be associated with custom payloads and are frequently leveraged to avoid detection by traditional anti-virus applications, as well as SIEMs that rely solely on static indicators. Since Todyl's Endpoint Security and SIEM leverage an advanced detection and analysis engine, our platform identified and prevented attempts to launch this malware. The platform also prevented any malicious behaviors that can indicate an attack is in progress.
Based on this knowledge, the team informed Ernest that it was suspected malware, as shown in Figure 1 below.
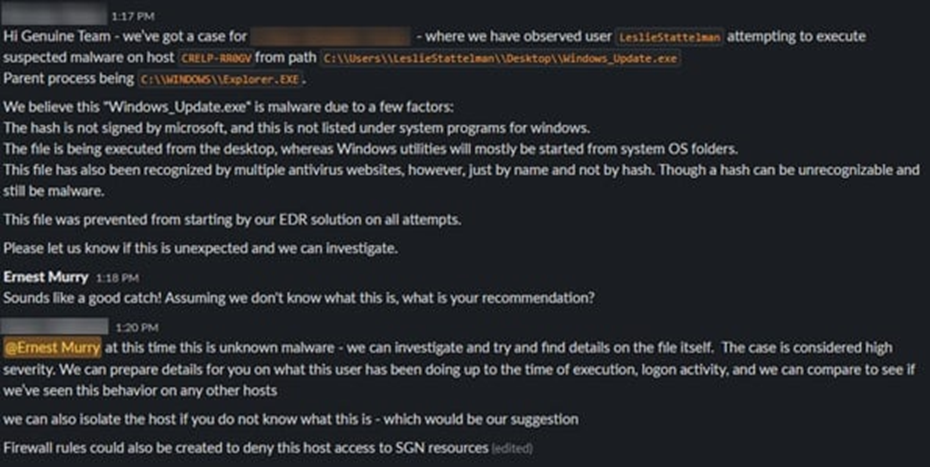
The MXDR team provided recommendations on how to respond, including isolating the host and implementing SGN Firewall rules to deny this host access to resources in the datacenter. SGN Firewall rules block all communication to and from the SGN, preventing access to the internet, data center, and other internal resources. This enables a safe investigation while mitigating the risk of lateral movement.
While communicating with Ernest via Slack, the team continued investigating and monitoring the host’s actions to see if similar activity occurred on other hosts within the client.
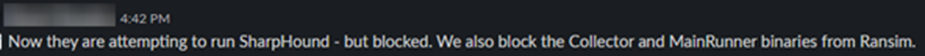
About halfway through the testing period, Ernest elevated the penetration tester’s user to a local administrator, which allowed them to launch a malicious reverse shell payload from the USB drives. By launching from the USB Drive, the penetration tester gained persistent access. Even then, the Ransomware, Malware, and Malicious Behavior Prevention modules included with Todyl’s NGAV blocked every payload and executable from running. The penetration tester also attempted to dump LSASS, but the process was blocked again.
Eventually, Ernest informed the MXDR team that this was part of a penetration test. Seizing the opportunity to practice with a real-world exercise, the MXDR continued to alert on and investigate every attempt.
Even with full physical system access and admin rights, Todyl’s Endpoint Security blocked the tester’s every move, and the MXDR team traced, tracked, and flagged all activity directly to Genuine via Slack (see Figures 2, 3, & 4 below).


What the results mean for Genuine
The results demonstrated that the layers of security Genuine implemented using the Todyl Security Platform performed as expected.
Throughout the test, Todyl’s MDXR team received 42 alerts as the tester tried different payloads and executables to break in, move laterally, and gain access to the data center. Despite all their efforts, the tester could not move laterally from the provided laptop, highlighting the effectiveness of combining Todyl’s integrated Endpoint Security with hands-on, expert support from Todyl’s MXDR team.
When a major client relationship and business reputation are at stake, real-time detections, comprehensive visibility, and continuous support from a team of dedicated security specialists are key. This level of engagement and expertise gave Genuine Technology Group confidence that Todyl would be there every step of the way during an attack.
Todyl’s comprehensive, unified security platform, including SASE, SIEM, Endpoint Security, and MXDR, work together to prevent, detect, and quickly respond to any threat. Learn how the Todyl Security Platform can help ensure you're protected in today's constantly evolving threat landscape.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



