Understanding initial access markets: Defense-in-depth
Initial access markets provide cyber criminals with a way to purchase and leverage stolen credentials for nefarious purposes. This blog will detail how you can defend against the threats posed by initial access markets and their associated credential theft.
This is the final part of our series on initial access markets; click here to read part one, describing their history. Click here to read part two on the techniques used by bad actors.
How to defend against initial access market-driven attacks
As described in the previous blog, there are many ways to leverage purchased credentials against an individual or organization. To combat them, you need to establish a defense-in-depth approach.
What is defense-in-depth?
Defense-in-depth describes a layered approach to security involving people, processes, and technologies (PPT) that work together in a concerted effort to prevent credential-based and other attacks. Although there are many aspects to a full defense-in-depth approach, here are some key facets to protecting against initial access market-driven attacks.
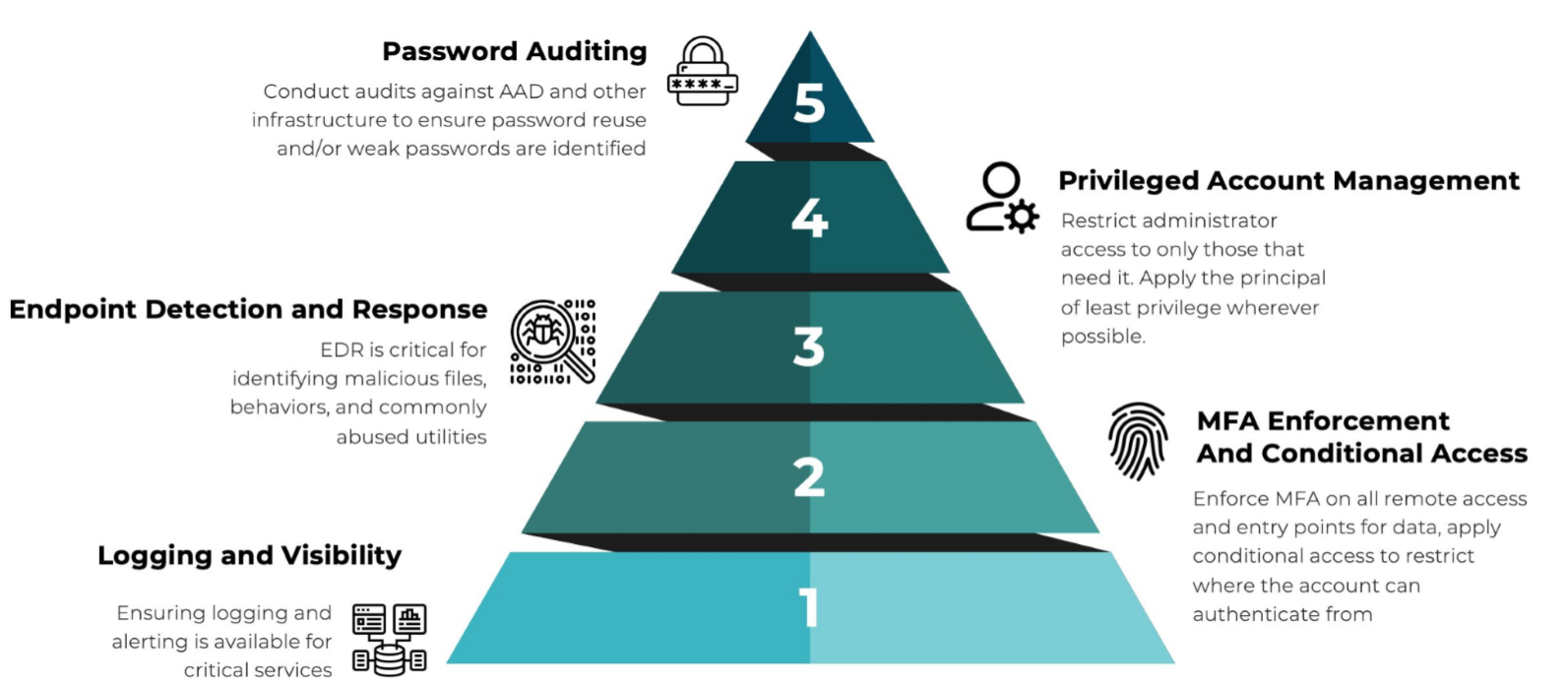
- Logging and visibility: The base of any strong security posture. Having a single pane of glass to review and investigate alerts and events allows you to quickly drill into issues and remediate them.
- Multi-factor authentication (MFA) enforcement and conditional access: Ensure users are who they claim to be. Add MFA to all critical authentications and prevent access based on policies (location, group, device, etc.) to lock down lateral movement within the network. MFA is no longer optional, so apply it wherever you can to prevent bad actors from achieving their goals.
- Endpoint detection and response (EDR): Collect information from your endpoints. EDR is the first line of defense against malware, ransomware, malicious files, and abused utilities. It also funnels information into your logging solution to centralize data.
- Privileged account management: Prevent unauthorized access to critical resources. Restrict admin access to only those who need it by the principle of least privilege.
- Password auditing: Ensure passwords are routinely refreshed. Develop strict password policies (length, complexity, rotation cycles, etc.) so that old, insecure passwords can’t be leveraged against the organization.
In practice, several solutions are required to achieve the various layers involved in a defense-in-depth approach. You can also explore a consolidated security platform to consolidate many of these requirements into a single solution. That way, you can leverage a single pane of glass to manage them all effectively at scale.
As stated before, these are only a handful of the layers involved in a defense-in-depth approach. Another crucial aspect is security awareness training. Covering the people side of PPT, your team needs to know that they are the first line of defense against attacks.
Especially with initial access markets, where phishing and business email compromise (BEC) are usual attack vectors, employees will receive the brunt of attacks. Be sure to train them on how to spot various forms of phishing like social engineering to keep them from clicking risky links or responding to attacker threats.
Learn more
As cybercrime continues to rise, initial access markets enable adversaries to operate quicker with more targeted attacks. By developing a defense-in-depth strategy, you and your organization can be better prepared to stop them in their tracks.
To learn more, hear from Todyl’s VP of incident response, Aaron Goldstein, as he describes the threat of initial access markets and how to address it in our webinar. Watch it here.
See Todyl in Action
Learn how you can protect what you built.
Stay on the Cutting Edge of Security
Subscribe to our newsletter to get our latest insights.



